IAM (Identity and Access Management) integration in cloud-native systems is complex but essential for securing modern IT environments. Here's why it matters and the challenges organizations face:
- Cloud-native systems rely on microservices, Kubernetes, and dynamic resources, requiring identity-based security rather than traditional network-based models.
- Common challenges include compatibility issues with older systems, inconsistent IAM policies across multi-cloud platforms, and managing a growing number of machine identities.
- Risks like credential sprawl, over-permissioning, and policy misalignment can lead to security vulnerabilities.
- Solutions include automation (e.g., Workload Identity Federation), centralized governance, and tools like Policy-as-Code and ML-based permission recommenders.
Organizations must adopt a structured, automated approach to IAM to ensure security, scalability, and efficiency in cloud environments.
Stop Struggling with Identity Management! Discover 5 Game-Changing Open-Source Tools!
sbb-itb-97f6a47
Common IAM Integration Challenges in Cloud-Native Systems
Organizations transitioning to cloud-native architectures often face tough obstacles when integrating Identity and Access Management (IAM) systems. These challenges arise due to technical mismatches, policy fragmentation, and operational inefficiencies that can delay deployments and expose security vulnerabilities.
Legacy Systems and Hybrid Integration Problems
Legacy systems bring their own set of issues to identity-centric security models. Many older applications lack support for modern protocols like SAML, OIDC, or SCIM. This forces businesses into a difficult decision: accept security risks or invest heavily in system upgrades. The situation becomes even more complicated when identities are scattered across AWS, Azure, GCP, SaaS platforms, and on-premises setups, creating isolated identity silos.
In hybrid environments, manual onboarding and offboarding processes often result in lingering "ghost accounts" - accounts that remain active but unused, posing security risks. Claire McKenna, Director of Content & Customer Marketing at ConductorOne, highlights the issue:
Traditional IAM wasn't built to solve the complexity of identity and access management today. Fragmented environments, skyrocketing non-human identities, and evolving attack techniques are exposing critical gaps.
The financial impact of these inefficiencies is significant. For example, each lost password costs around $70 when factoring in security verification and lost productivity.
Multi-Cloud IAM Policy Inconsistencies
Each cloud provider - AWS, Azure, and others - uses its own IAM model, requiring manual adjustments that can create security blind spots. For instance, AWS might use "ServiceAccessLevel", while Azure employs "WorkloadAccessTier", leading to mapping errors that teams must fix manually. This lack of alignment between platforms is a core issue, as IAM systems are designed to operate independently without cross-platform standards.
In decentralized multi-cloud setups, "secrets sprawl" becomes a growing concern. Credentials often move across environments without consistent enforcement of policies. If stolen, these credentials can grant unauthorized access to systems they were never meant to interact with. To manage this, teams frequently create new IAM policies for each environment, resulting in redundant configurations, slower deployments, and higher operational costs. These inefficiencies make scaling IAM in agile DevOps environments even more challenging.
Scalability and DevOps Misalignment
The complexity of multi-cloud IAM policies doesn’t just slow down deployments - it also clashes with the fast-paced nature of modern DevOps workflows. Traditional IAM systems act like gates, creating bottlenecks in environments that require speed and flexibility. In contrast, cloud-native systems need IAM to serve as "guardrails", which allow teams to move quickly while staying within secure boundaries. When these processes don't align, rapid deployments can lead to unchecked role and policy sprawl, weakening security.
The scale of the problem is immense. Over the next 12 months, the number of human and machine identities is projected to grow by 240%. At the same time, identity-based techniques are involved in roughly 80% of cyberattacks. Slow IAM processes often push business units to bypass security measures to meet deadlines, resulting in shadow IT and increased risks of data breaches.
Practical Solutions for IAM Challenges in Cloud-Native Systems
Addressing IAM challenges in cloud-native systems often comes down to automation and standardization. By replacing manual workflows with automated processes, organizations can boost both security and efficiency. The focus shifts from static credentials and scattered policies to a unified, code-driven approach to governance.
Identity Abstraction and Automation
Workload Identity Federation (WIF) is a game-changer for managing credentials. Instead of juggling long-lived service account keys, WIF allows external credentials from providers like AWS, Azure, or GitHub to be exchanged for short-lived, federated tokens automatically. As Google Cloud puts it:
Workload Identity Federation eliminates the maintenance and security burden associated with service account keys.
Another helpful tool is machine learning recommenders, which simplify permission management. These systems analyze how permissions are actually used, suggesting optimizations to ensure roles follow the principle of least privilege without requiring extensive manual audits. This is especially important as 42% of security leaders prioritize IAM security, with the Cloud Infrastructure Entitlement Management (CIEM) market projected to hit $7.5 billion by 2028.
Policy-as-Code brings IAM policies into the same CI/CD pipelines developers already rely on. By managing policies as version-controlled code, organizations can run automated tests to identify misconfigurations quickly. For instance, AWS IAM Access Analyzer uses mathematical inference to detect unintended public or cross-account access in seconds.
Automated lifecycle management tackles privilege creep by using conditional role bindings and expiration dates for group memberships. This ensures temporary access is automatically revoked when no longer needed, eliminating the hassle of manual tracking. Adding attribute-based conditions with Common Expression Language (CEL) further enhances control. For example, you could limit GitHub Actions to access only specific repositories.
These tools collectively establish a strong foundation for centralized IAM in cloud environments.
Unified Governance and Real-Time Policy Enforcement
These solutions directly address fragmented policies and manual processes, making governance more streamlined and effective.
Centralized identity management starts with a single Identity Provider (IdP) - such as Okta, Azure AD, or Google Workspace - that acts as the "single source of truth." This IdP federates identities across all cloud platforms, enabling Single Sign-On (SSO) and centralized offboarding. As PeakHour explains:
The cornerstone of any multi-cloud IAM strategy is to have a single source of truth for identity.
Just-in-Time (JIT) access ensures elevated privileges are granted only when required and for a limited period. Tools like Azure AD Privileged Identity Management (PIM) or AWS session policies automate this process, ensuring permissions expire automatically. This approach addresses the common issue where users are given far more access than they actually need.
Organization-wide guardrails prevent local administrators from bypassing security policies. Features like AWS Service Control Policies (SCPs) or Azure Blueprints enforce maximum permission limits across all accounts. Coupled with continuous monitoring through Security Information and Event Management (SIEM) systems, these guardrails consolidate logs from AWS CloudTrail, Azure Monitor, and GCP Audit Logs into a single view for real-time anomaly detection.
| Feature | Traditional IAM | Cloud-Native IAM (CIEM/WIF) |
|---|---|---|
| Credential Type | Long-lived keys/passwords | Short-lived federated tokens |
| Management | Manual rotation and auditing | Automated ML-based recommendations |
| Visibility | Assigned permissions (on paper) | Effective permissions (actual reach) |
| Scaling | Manual policy updates | Policy-as-Code and automated pipelines |
| Trust Model | Static trust | Dynamic, attribute-based access (ABAC) |
Attribute-Based Access Control (ABAC) further simplifies permission management by dynamically granting access based on tags like CostCenter, Project, or Region. This reduces the need for static roles and allows teams to adjust access by modifying group memberships instead of rewriting individual policies. The result? Faster onboarding, smoother transitions, and fewer configuration errors - laying the groundwork for a systematic implementation of these solutions.
Implementation Framework for IAM Integration
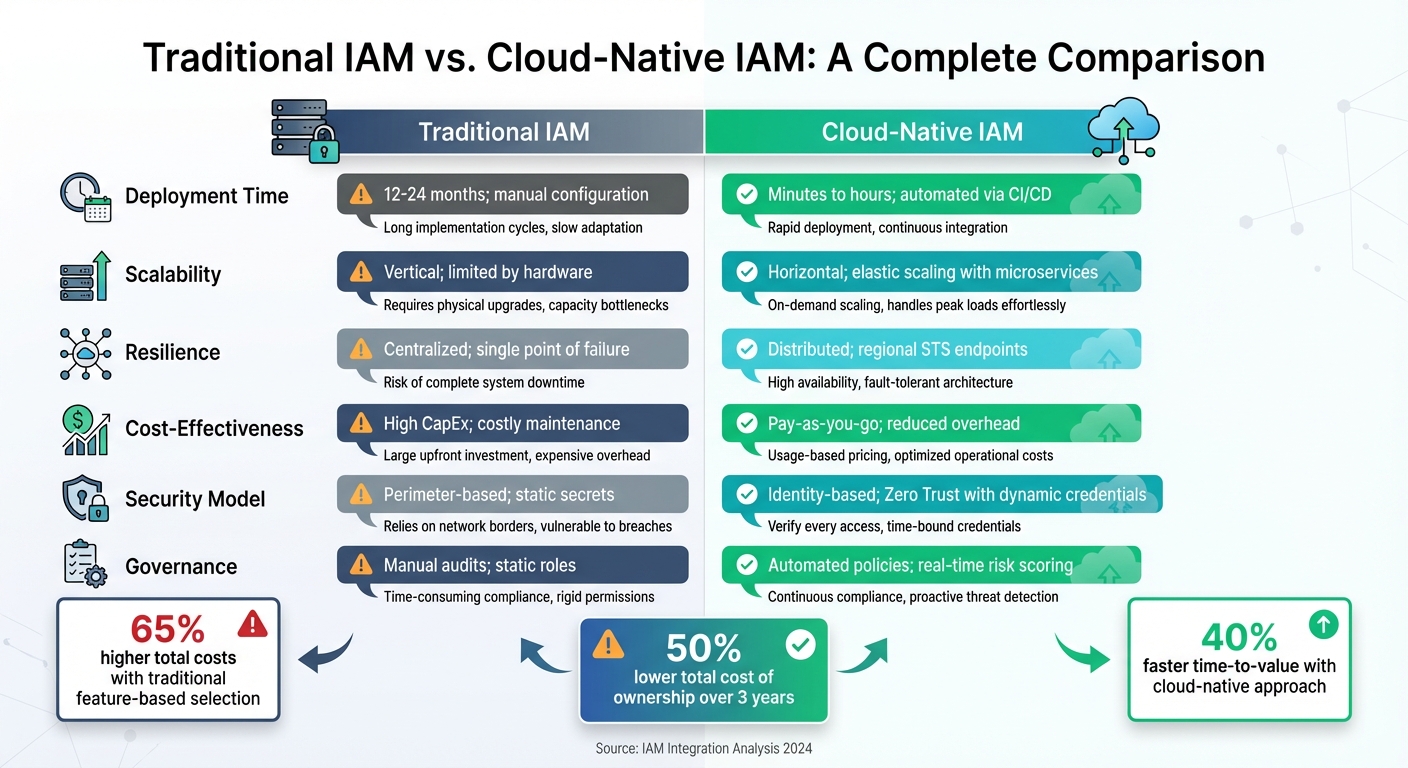
Traditional IAM vs Cloud-Native IAM: Key Differences and Benefits
To ensure secure and efficient IAM integration, organizations need a structured framework. This approach moves beyond treating IAM as a one-time setup, focusing instead on making it an ongoing, systematic process. Companies that adopt this strategy can see 40% faster time-to-value and 50% lower total cost of ownership over three years compared to those relying on traditional feature-based checklists.
Step-by-Step IAM Integration Process
A well-defined framework simplifies the transition to secure, cloud-native IAM solutions. Here's how to approach it:
Begin by creating an inventory of all users, workloads, and third-party entities. Map out inbound (external-to-internal) and internal (within-system) data flows. Microsoft emphasizes the importance of this step:
Identity is always the primary perimeter. This scope doesn't just include the edges of your workload. It also includes individual components that are inside your workload.
Once you have full visibility, standardize authentication protocols. Use SAML 2.0 for web applications and OIDC with OAuth 2.0 for microservices and mobile designs. These protocols eliminate the need for custom authentication logic, ensuring compatibility across systems. Next, adopt identity abstraction by replacing static service keys with short-lived tokens. This can be achieved through Workload Identity Federation, allowing external workloads (e.g., AWS, Azure, GitHub Actions) to access cloud resources securely with temporary tokens.
To enforce security, define a policy framework using Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC). This ensures access is granted on a least-privilege basis. Additionally, integrate observability by connecting IAM logs to a centralized SIEM platform like Datadog Cloud SIEM or Microsoft Sentinel. Enable data access logging for all IAM and Security Token Service APIs to maintain a reliable audit trail. Real-time monitoring can then help detect anomalies before they escalate into larger issues.
By following these steps, organizations can unify governance, automate policy enforcement, and scale their systems securely, highlighting the advantages of cloud-native IAM over traditional approaches.
Comparison Table: Traditional vs. Cloud-Native IAM
The move to cloud-native IAM transforms how organizations manage identity systems, offering automation, scalability, and improved security compared to traditional methods.
| Metric | Traditional IAM | Cloud-Native IAM |
|---|---|---|
| Deployment Time | 12–24 months; manual configuration | Minutes to hours; automated via CI/CD |
| Scalability | Vertical; limited by hardware | Horizontal; elastic scaling with microservices |
| Resilience | Centralized; single point of failure | Distributed; regional STS endpoints |
| Cost-Effectiveness | High CapEx; costly maintenance | Pay-as-you-go; reduced overhead |
| Security Model | Perimeter-based; static secrets | Identity-based; Zero Trust with dynamic credentials |
| Governance | Manual audits; static roles | Automated policies; real-time risk scoring |
Organizations relying on feature-based selection often encounter 65% higher total costs due to unexpected implementation and customization expenses. In contrast, the cloud-native model minimizes these costs with automation and managed services, making it a more secure and efficient choice for modern enterprises.
Using Expert Consulting for IAM Optimization
How Expert Consulting Improves IAM Success
Integrating Identity and Access Management (IAM) into cloud-native systems is no small feat - it demands a level of expertise that goes beyond basic IT knowledge. With identity-based techniques now playing a role in about 80% of cyberattacks, relying on improvised methods can lead to costly mistakes. This is where expert consultants come in, offering tried-and-tested frameworks and vendor-neutral advice that minimize risks and ensure smooth implementation.
For example, consultants often deploy tools like identity proxies or Privileged Access Management (PAM) solutions to bridge the gap for legacy systems. They also implement policy-as-code frameworks to maintain consistent enforcement across multi-cloud environments like AWS, Azure, and GCP. These approaches aren't just theoretical - they're backed by real-world success stories.
Take PwC’s massive IAM transformation project, completed in April 2023. The initiative consolidated 13 separate platforms and 90 Active Directory forests into a single cloud-based system. This overhaul affected 350,000 internal users and approximately 2 million external users. The results? User registration times dropped from 4–8 hours to just 5 minutes, and login activity tripled within two years. As a PwC representative explained:
"There was no playbook for this. We had to create one. We worked together to build a global solution and successfully delivered on our design and security principles."
- PwC Network Representative
Beyond the technical side, consultants help streamline operations by automating lifecycle management. By integrating IAM with HR systems, they eliminate orphaned accounts and cut administrative workloads by up to 50% through effective Role-Based Access Control (RBAC). These operational and technical advantages make partnering with the right expert a critical decision.
Finding IAM Experts Through Top Consulting Firms Directory
Choosing the right consulting partner goes beyond picking a big-name brand. The focus should be on firms that offer vendor-agnostic support, ensuring that tools like SailPoint, Okta, or Microsoft Entra ID are selected based on your company’s specific needs - not a consultant’s vendor ties. Seek out firms that provide a complete service package, from initial assessments and application onboarding to ongoing managed services that keep policies aligned over time.
The Top Consulting Firms Directory (https://allconsultingfirms.com) is a valuable resource for finding these experts. It connects organizations with vetted consultants who specialize in complex IAM integrations for cloud-native systems. The directory allows you to filter firms by industry expertise, certifications, and geographic reach, making it easier to identify the right partner for your needs in areas like cybersecurity, IT infrastructure, and digital transformation.
When using the directory, bring in stakeholders from IT, security, HR, and business units early in the process. IAM isn't just a technical initiative - it requires input from across the organization to ensure success. Start by identifying your most critical systems, or "crown jewels", and prioritize these during implementation. This risk-based approach ensures consultants focus on high-impact areas first, creating momentum for broader adoption.
Conclusion
IAM integration plays a critical role in securing modern cloud environments. With identity-based attacks becoming increasingly common, relying on outdated perimeter defenses is no longer sufficient. The shift from network-focused security to an identity-first approach fundamentally changes how organizations protect their cloud infrastructure.
Managing identities across platforms like AWS, Azure, and GCP introduces challenges such as inconsistent policies, outdated systems that lack support for modern protocols, and inadequate oversight of non-human identities. These issues highlight the need for practical and automated solutions.
Adopting effective IAM practices can deliver measurable outcomes. For instance, centralizing identity data and automating lifecycle management can reduce administrative tasks by up to 50% while significantly shrinking the attack surface. Organizations that consolidate identity data into a single source of truth are 50% more likely to automate access successfully, transforming provisioning processes from days to mere minutes. Additionally, replacing standing privileges with temporary, auto-expiring permissions helps eliminate persistent access points that attackers often exploit.
Expert guidance can accelerate IAM optimization. Claire McKenna from ConductorOne emphasizes:
If security measures are too cumbersome, users will find ways to bypass them. A modern IAM strategy must be both secure and frictionless.
Partnering with experienced consultants can make all the difference. These professionals bring vendor-neutral frameworks, tested methodologies, and the strategic insight needed to navigate complex IAM challenges. Resources like the Top Consulting Firms Directory can help connect you with experts who can guide your organization toward a more secure identity management strategy.
FAQs
How do I integrate IAM with legacy apps that don’t support SAML or OIDC?
To connect IAM with older applications that don’t support SAML or OIDC, you can rely on legacy authentication methods such as Web Access Management (WAM) solutions. Another option is to use identity federation or proxy solutions, which allow centralized access control and enable single sign-on (SSO) for these outdated systems. These methods act as a bridge, ensuring modern IAM systems can work seamlessly with legacy software.
What’s the fastest way to standardize IAM policies across AWS, Azure, and GCP?
To quickly streamline identity and access management (IAM) across platforms like AWS, Azure, and GCP, consider using a centralized identity provider (IdP) such as Azure AD, Okta, or Google Workspace with federation. Pair this with a unified policy framework - tools like OPA (Open Policy Agent) work well for this purpose. This combination allows you to enforce consistent controls and maintain standardized IAM policies across all platforms, ensuring efficient and cohesive management.
How can we reduce machine-identity sprawl without slowing down DevOps?
To keep machine-identity sprawl under control while preserving the fast pace of DevOps, focus on using dynamic, short-lived identities and centralized management. For example, ephemeral credentials - like Kubernetes service account tokens or cloud-native integrations - help avoid the accumulation of static credentials. Combine these with federation-based identity management and automation tools to simplify provisioning and ensure seamless rotation. This method not only boosts security and reduces sprawl but also allows DevOps teams to maintain their efficiency without sacrificing agility.


